Data Theft
A speculative inquiry into a near-future of wearable technology. Sponsored by Intel's Design Network and working with Tim Kim, we created wearable devices for the theft of personal data.
Featured In
htxt.africa “The (Offbeat) Future of Wearables”
SCPR “5 cool ‘wearable’ prototypes that might be the next Google Glass”
Russia-1 Morning Story
PoC by:
Tel Aviv University
Body Language
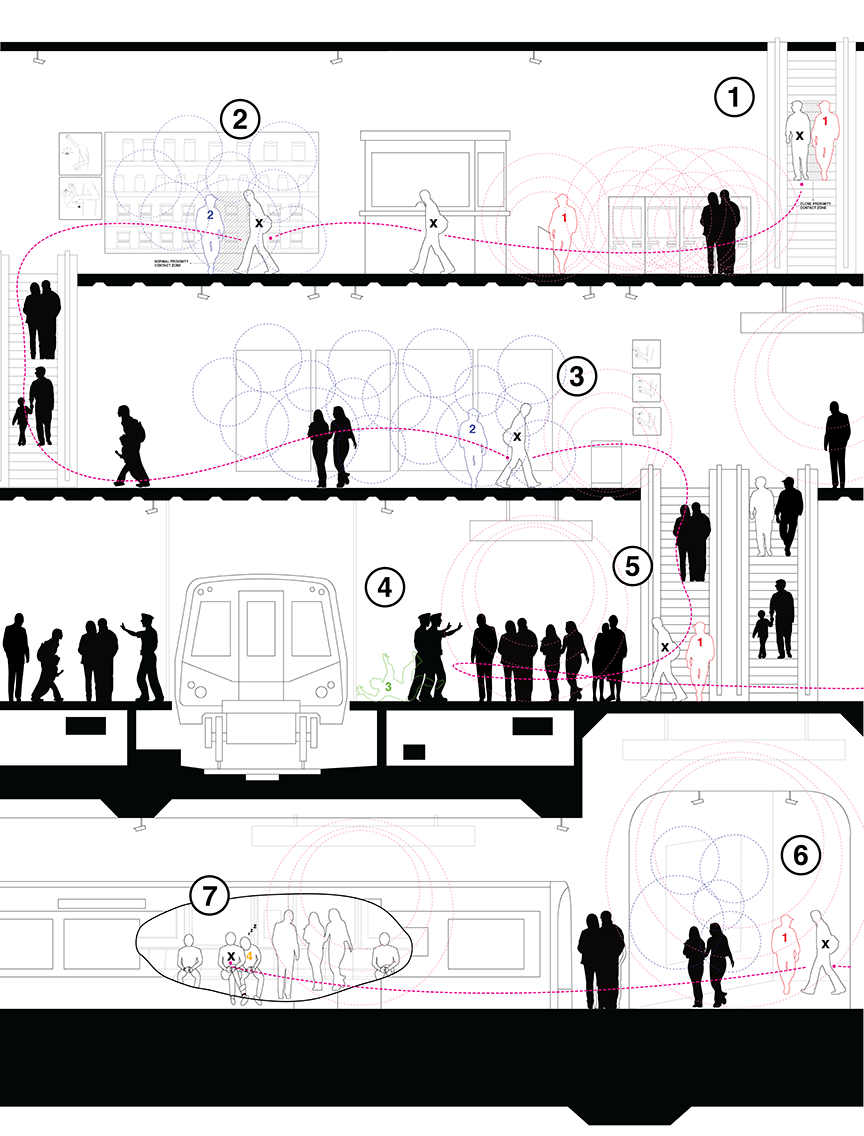
Our future is connected. Devices in our hands, on our bodies, and in the environment will all connect and communicate “seamlessly,” while vulnerabilities in our networks provide opportunities for the misdirection and theft of data. As contextual games become the norm and we come to interact more fluidly with the built environment, rogue users are able to use “bizarro” inverted wearable devices to steal private information. Using the psychology of pickpockets and exploiting flaws in existing internet infrastructure, MALWAReABLES exposes extreme vulnerabilities in the connected environment.
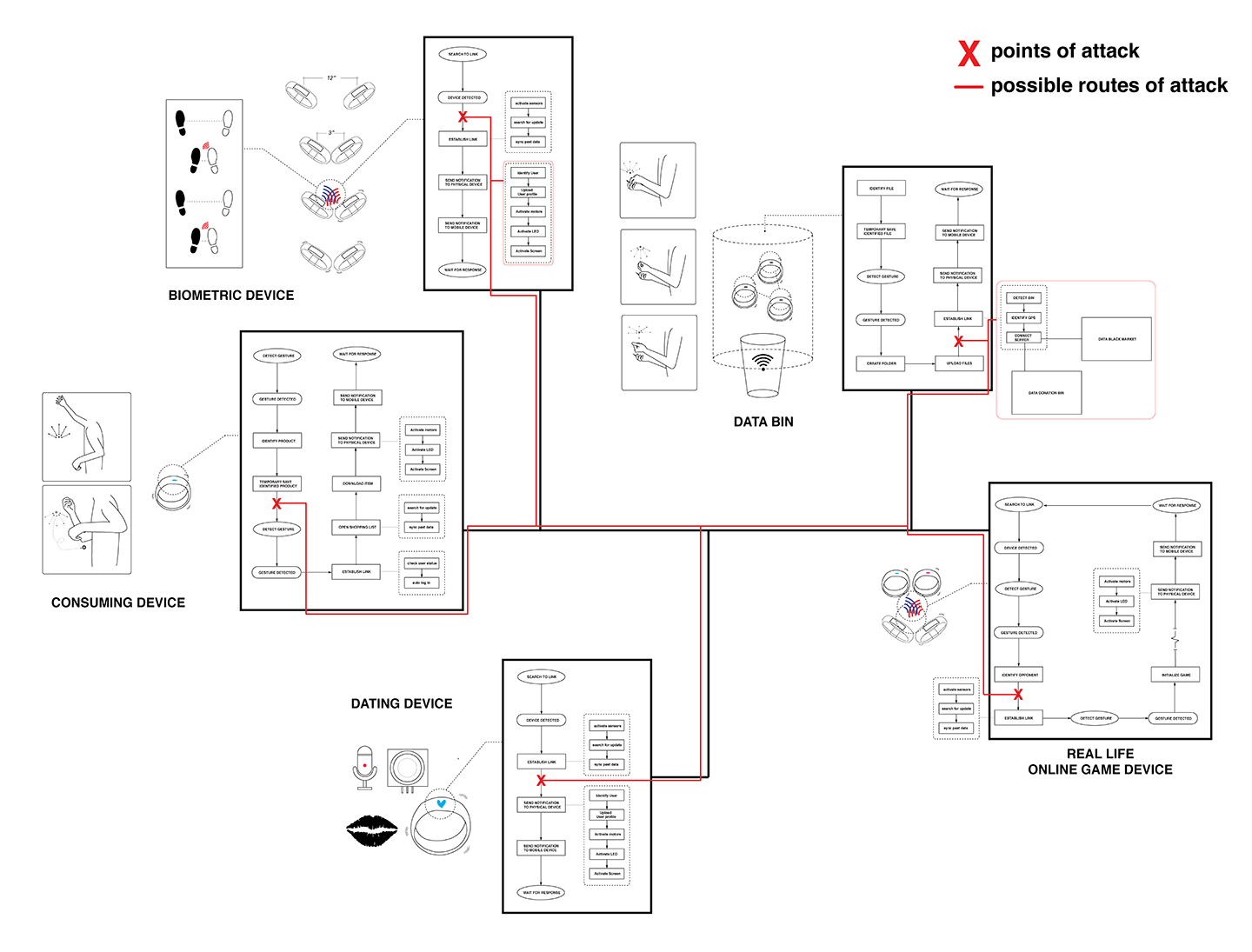
We imagined some contextual games and interactions that could be possible in the connected future. There's a shopping experience with no goods and a dating tool that taps into global data streams, as well as other situations that rely upon seamless connectivity. We based the interactions of "gestural skeuomorphism," a term we coined to address the need for new metaphors for interactions using wearable devices.
Kissing the Dog
With elaborate counter-maps, the rogue agents are able to misuse the city without "kissing the dog," or drawing attention to themselves. Pickpockets case the location, creating an elaborate plan of action. The unsuspecting victim is identified before even entering the station, and serendipitous events are totally staged. A diversion is created, becoming an easy conversation topic for the pickpocket and the victim, making the transfer of viruses effortless.
Using psychology, the thief disrupts a victim's attention digitally and physically. Armed with a set of "bizarro devices," the thief distracts the user and activates their wearable devices, before connecting and making illicit transactions.
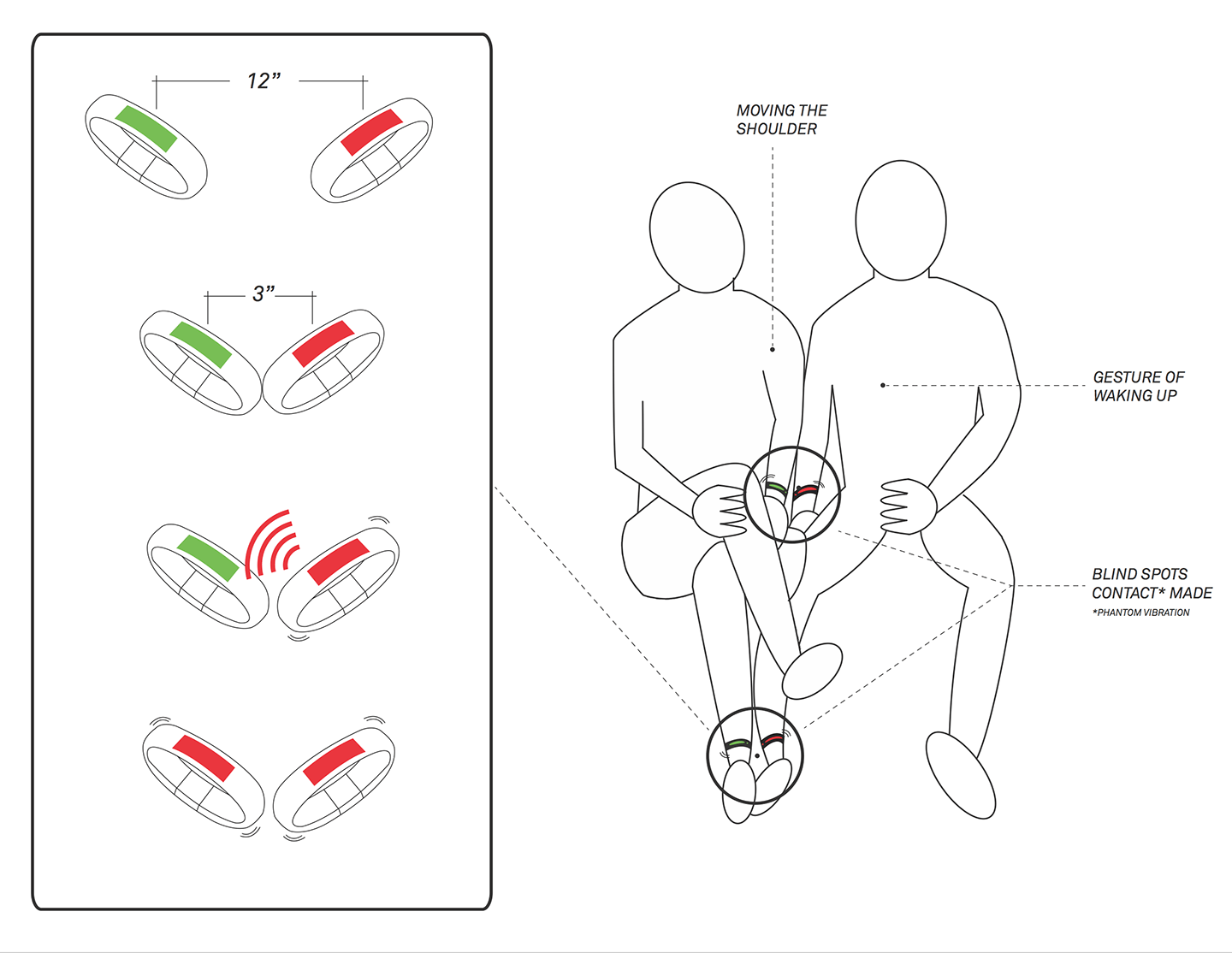
Ghost Vibrations
The pickpockets' goal is data generated by oversimplified wearable devices. Pickpockets have to activate various sensors around your body by "feigning" interaction, and once it connects to phone, malware is uploaded to a device through a quick and subtle physical gesture. By monitoring radio frequencies while contact with the victim's device is made, the pickpocket is able to discern and decode the actual bits traveling across circuitry.
This opens an interesting avenue of investigation. The oversimplification of our devices and interfaces leaves ambiguities to be exploited, while flaws in the infrastructure that the technology is founded upon allow for misuse. Things like quantification become risky, and the risk is amplified when the devices that store our most personal data are carried on our extremities.
Personal
arduino
electronics
concept development